Smarter Sorting Security and AI Governance
At Smarter Sorting, safeguarding your data and using Artificial Intelligence (AI) responsibly are at the heart of everything we do. We leverage secure cloud infrastructure, rigorous security controls, and transparent AI governance to deliver solutions you can trust. Security and AI governance aren’t just checkboxes for us. They’re ongoing, company-wide commitments. We continually refine our practices to keep your data safe and ensure we deliver responsibly, every time.
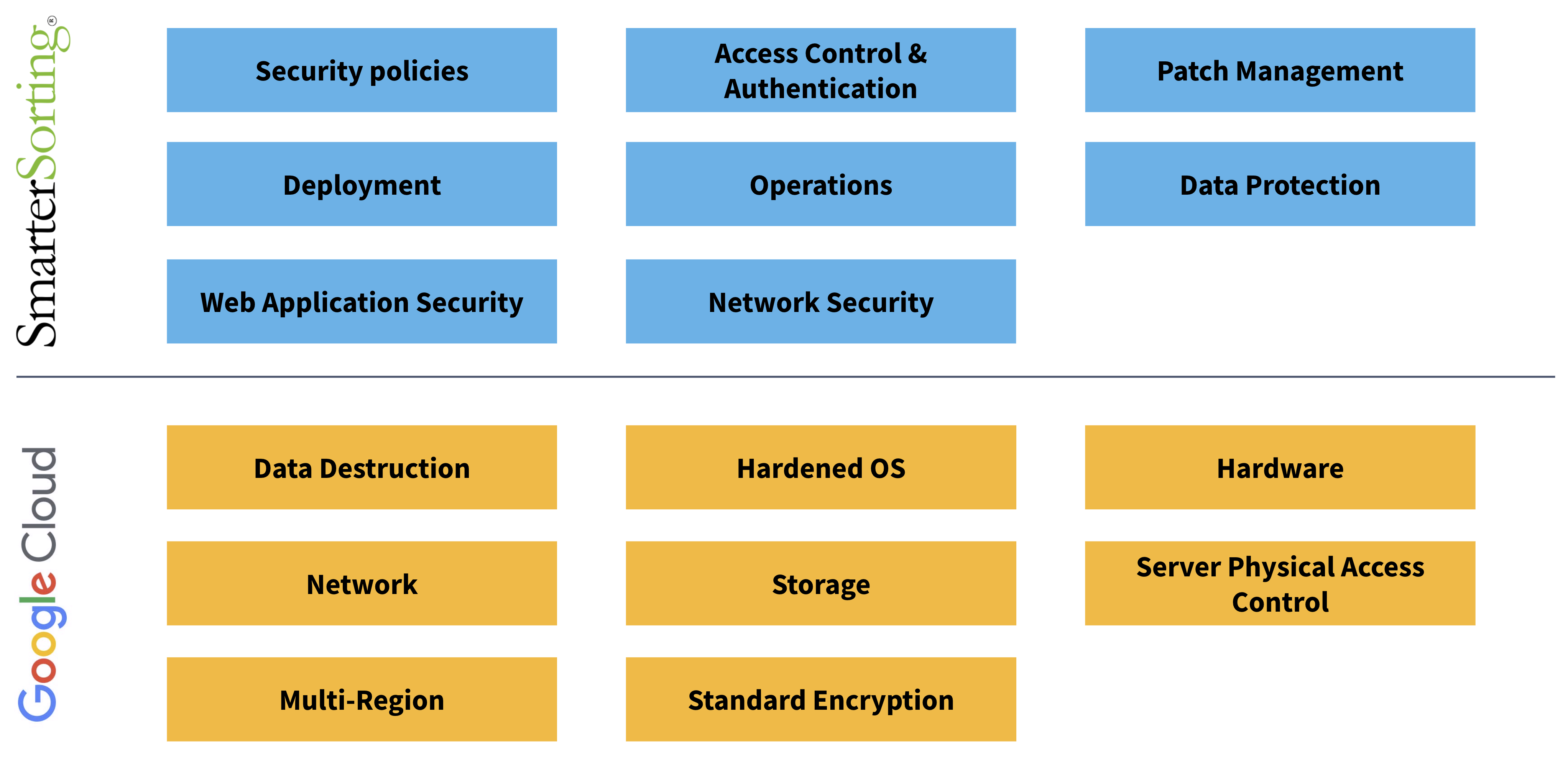
Access & Authentication
- Single Sign-On (SSO) and Multi-Factor Authentication (MFA) for secure access.
- Session timeouts and account lockout policies.
- Least Privilege model with quarterly access reviews.
- Privileged access to production systems restricted to authorized personnel only.
Data Protection
- Encryption at Rest: AES-256 (Google Cloud native encryption)
- Encryption in Transit: TLS 1.2 or higher
- Logical data segregation by customer ID
- GCP-managed encryption keys with optional key rolling
- Company-issued devices with enforced encryption and endpoint security
Infrastructure & Network Security
- 100% cloud-hosted on Google Cloud Platform (GCP) across two US regions and six zones
- Firewalls and Web Application Firewall (WAF) to block malicious traffic
- DMZ architecture with load balancers isolating internal systems
- Segregated virtual networks via distinct GCP VPCs
Operational Resilience
- Disaster Recovery:
- Daily encrypted backups to a secondary region
- Monthly restore tests for data integrity
- Immutable infrastructure with every deployment
- RPO: 24 hours | RTO: 24 hours
- Business Continuity Planning: Tested annually with documented lessons learned
- High Availability: 99.9% SLA with redundant classification systems
Monitoring & Incident Response
- Real-time monitoring of application and infrastructure health
- Comprehensive audit logging for sensitive actions (retained 15 months)
- Automated alerts to engineering and security teams for immediate action
- Documented incident response plan, tested annually through simulated exercises
- Breach notifications issued within 24 hours of detection
Risk Management & Compliance
- SOC 2 Type II attested
- Annual penetration testing and continuous vulnerability scanning
- Formal risk assessment process, updated annually, covering operational, technical, and vendor-related risks
- Third-party vendor management program with contractual security requirements and periodic audits
- Regulatory Compliance:
- CCPA Compliant
- GDPR/HIPAA: Not applicable (no EU citizen or PHI data processed)
- Privacy & Cybersecurity insurance coverage
AI Governance
Responsible AI Use
- The Smarter-1 platform does not process personal data (PII).
- Customer-specific data remains private, with masking options for proprietary inputs.
- No proprietary data is shared with public AI models.
Trusted Data Sources
Our AI only uses publicly available product information, such as:
- Product names and ingredient lists
- Physical attributes (e.g., pH, flashpoint, battery chemistry)
- Data collected via APIs, web scraping, or supplier-provided public sources
How Our AI Works
- Closed-Loop AI is our standard approach, ensuring privacy and security.
- Embedding Models identify product similarities and power Retrieval Augmented Generation (RAG).
- Large Language Models (LLMs) like GPT-5, Gemini, and Llama 2 support rules-based reasoning.
- Vector Search tools (Elasticsearch, Supabase, Nomic.ai) provide fast, precise retrieval.
- Proprietary Confidence Algorithms check accuracy and reduce risks of incorrect outputs.
Training & Quality Assurance
- Human experts create and validate training datasets.
- Models are tested and refined in collaboration with customers to ensure business alignment.
- Built-in safeguards against bias and “hallucinations” include:
- Disagreement detection between classifiers
- Neighbor-agreement consensus rules
- Logical rulesets constraining AI outputs
Governance & Oversight
- Data Ownership: Customer classifications are only shared with that customer.
- Proprietary Logic Protection: Unique business rule logic is secured through masking and access controls.
- Continuous review ensures accuracy, compliance, and ethical AI use.
Contact
For more information, or if you have any questions, please reach out to security@smartersorting.com.
*Note: For portal-related incidents, please contact Customer Support first for triage.